Federate IdP authentication through enterprise AD
In some enterprise scenarios, direct integration between an external Identity Provider (IdP) and an internal Active Directory (AD) is not feasible—often due to security concerns or network isolation. To solve this, a RESTful API-based authentication delegation approach can be used.
Example for federating with enterprise AD
PS:SiX IDaaS & IAM IDP federated with enterprise AD, before sign in its ERP, employees trigger AD sign in through click the button "Login with "SiX INNO" AD account"!
TIP
After federation, your IdP user will benefit from MFA, personal information sharing consent control, more at: Overview of Data Security & Privacy
TIP
Authentication federation refers to authentication delegation. After the Identity Provider (IdP) in the SiX IDaaS & IAM tenancy receives the authentication request, it delegates the request to the enterprise AD.
Steps to federate IdP authentication through enterprise AD
1. Create an SiX IDaaS & IAM IdP(identity application) tenant
On SiX IDaaS & IAM console, go to "Authentication -> Create Identity Application" to create an IdP(identity application) tenant, change the "Authentication Sources:" to "Outside authentication source(http/https endpoint)".
2. Set the federated IdP parameters
Set the Restful IdP parameters, point the Restful endpoint to the proxy endpoint. 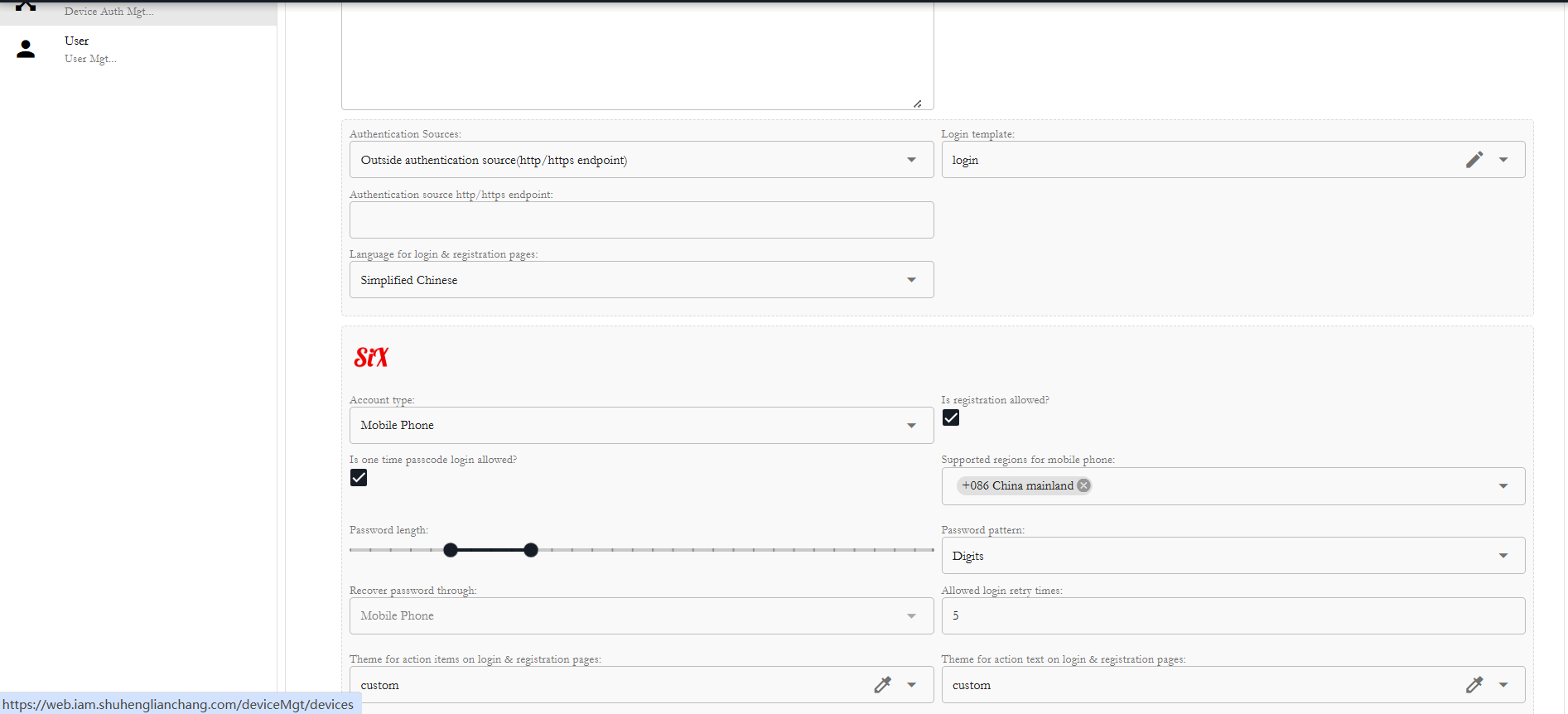
WARNING
When the IdP is created, an RSA 256 private key will be generated once to let the IdP owner to download it, the following authentication data flow between SiX IDaaS & IAM and the restful endpoint will be encrypted through the public key.
3. Create an OAuth2 Client tenant and associate it with IdP tenant
Creaate an OAuth2 Client tenant on the SiX IDaaS & IAM console and associate it with IdP(identity application) tenant.
4. Use the OAuth2 Client in your application
Apply the OAuth2 Client tenant information in your application to initiate the authentication process, when the authentication process is triggered, SiX IDaaS & IAM will handle the authentication federation process automatically.
5. Your application get ID information and associate it with your local user ID
You can get the IdP tenant "openId" and the ID of federated Restful provider user through parsing JWT and use /userinfo endpoint.
6. Use SiX IDaaS & IAM sample/SDK to quickly implement the Restful endpoint
SiX IDaaS & IAM will provide the sample code/sdk to let the IdP owner to quickly connect to enterprise AD through LDAPS.