Federate IdP with OIDC IdP
OIDC(Open Id Connect) is an open authentication protocol that enables users to sign in to multiple applications using a single set of credentials.
If you've already developed applications using your own OIDC Identity Provider (IdP), you can federate this IdP with the one provided by the SiX IDaaS & IAM Identity Application. By enabling authentication federation, users can log into your new application using their existing OIDC IdP credentials, while authorization is centrally managed through the IAM system within the SiX IDaaS & IAM console.
TIP
After federation, your IdP user will benefit from MFA, personal information sharing consent control, more at: Overview of Data Security & Privacy
TIP
Authentication federation refers to authentication delegation. After the Identity Provider (IdP) in the SiX IDaaS & IAM tenancy receives the authentication request, it delegates the request to the existing OIDC IdP.
Steps to federate IdP with OIDC IdP
1. Create an SiX IDaaS & IAM IdP(identity application) tenant
On SiX IDaaS & IAM console, go to "Authentication -> Create Identity Application" to create an IdP(identity application) tenant, change the "Authentication Sources:" to "OIDC authentication source(identity provider)".
2. Set the federated IdP "OIDC/OAuth2 client" parameters
Set the federated IdP "OIDC/OAuth2 client" parameters as "Client ID", "Client Secret" etc. 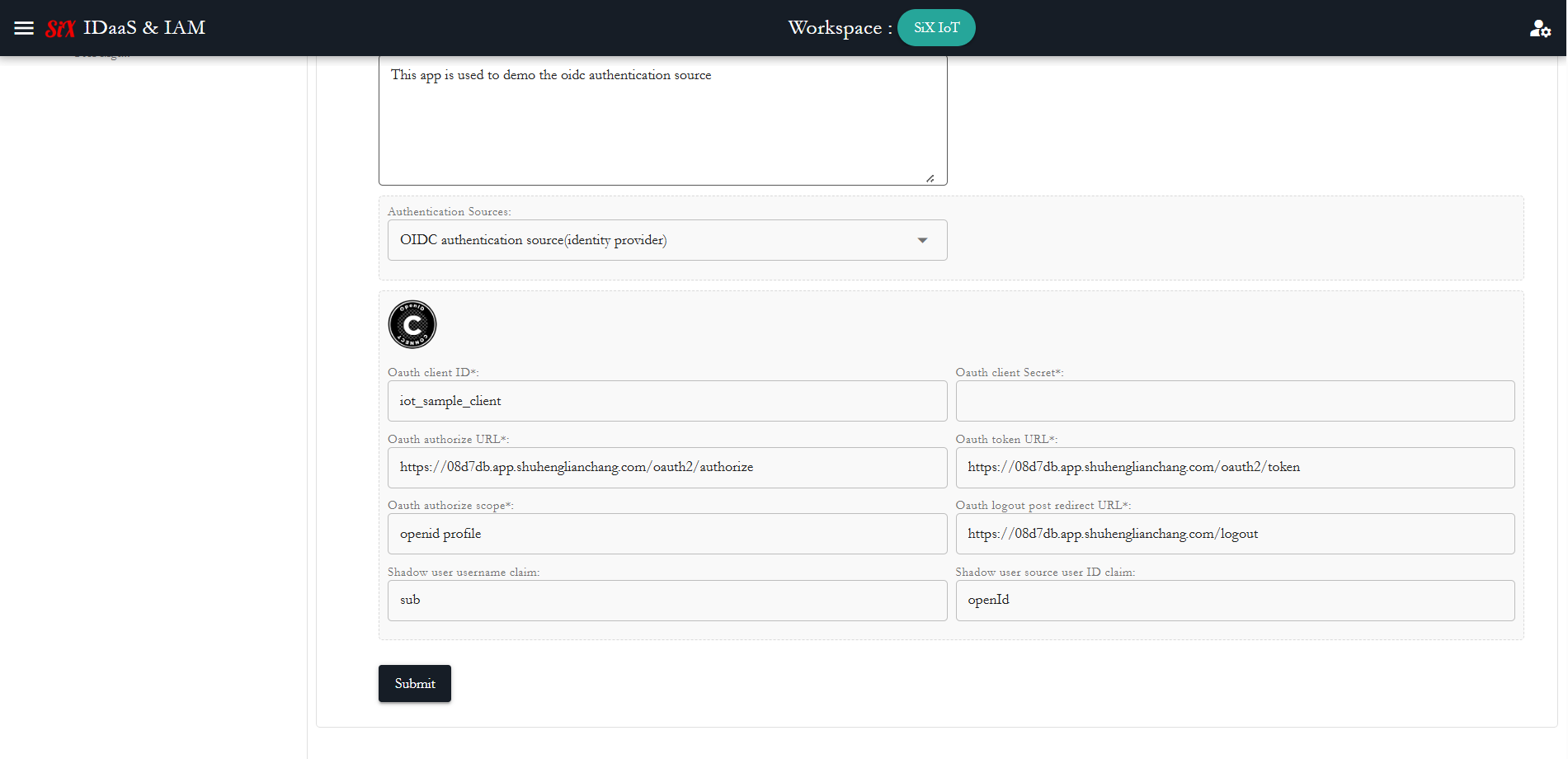
WARNING
Currently only support to parse the ID Token and Access Token in JWT format!
WARNING
Please ensure to set the "authorization code" callback URL of the federating IDP to federated IDP, Url is: “https://{appDomain}/oidc/sso/callback”!
3. Create an OAuth2 Client tenant and associate it with IdP tenant
Creaate an OAuth2 Client tenant on the SiX IDaaS & IAM console and associate it with IdP(identity application) tenant.
4. Use the OAuth2 Client in your application
Apply the OAuth2 Client tenant information in your application to initiate the authentication process, when the authentication process is triggered, SiX IDaaS & IAM will handle the authentication federation process automatically.
5. Your application get ID information and associate it with your local user ID
You can get the IdP tenant "openId" and the ID of federated OIDC provider user through parsing JWT and use /userinfo endpoint.
TIP
A sample access token with "openId" and federated attributes(including the federated IDP user id) highlighted!
{
"sub": "abceft@six-inno.cn",
"role": [
{
"ROLE_iam-iot-product-key": [
"iam_config_read",
"iam_key_create",
"iam_keys_read",
"iam_key_update"
]
},
{
"ROLE_iam-iot-app-edit": [
"iam_app_update",
"iam_app_create",
"iam_app__client__link_remove"
]
},
{
"ROLE_iam-iot-product-edit": [
"iam_iot__product__props_create",
"iam_iot__product_update",
"iam_iot__product__topic_delete",
"iam_iot__product__topic_create",
"iam_iot__product_delete",
"iam_iot__product_create"
]
},
{
"ROLE_iam-iot-device": [
"iam_iot__device__mqttmsgs_read",
"iam_iot__analysis_deviceMsg",
"iam_iot__device__statuses_read",
"iam_iot__device__info_bindings",
"iam_iot__device__info_acls",
"iam_iot__device_bind",
"iam_iot__analysis_activeDevice"
]
},
{
"ROLE_iam-iot-product-read": [
"iam_iot__product_read",
"iam_iot__products_read"
]
},
{
"ROLE_iam-iot-app-read": [
"iam_app__clients_read",
"iam_app_read",
"iam_app__users_read",
"iam_apps_read"
]
},
{
"ROLE_iam-iot-client-read": [
"iam_clients_read"
]
},
{
"ROLE_iam-device": [
"iam_device_read",
"iam_devices_read",
"iam_device_registration",
"iam_device__guid_read",
"iam_device_provision"
]
},
{
"ROLE_iam-iot-config-read": [
"iam_iot__config_read"
]
},
{
"ROLE_iam-iot-client-edit": [
"iam_client__app_create",
"iam_client_create",
"iam_client_update"
]
}
],
"org": {
"level": 1,
"orgId": "c0a81f4c-91a8-1e4f-8191-a82e66b50000"
},
"openId": "ac1e2001-976d-15de-8197-6d181c780001",
"iss": "http://127.0.0.1:9001",
"aud": "iot_sample_client",
"nbf": 1749957697,
"federate": [
{
"name": "oidcAuthn",
"value": "{\"access_token\":\"eyJraWQiOiJiYmQ4ZDg0NS0yZTY0LTQxYzQtYTk4NC03Mjg0OWY2OTI1NzIiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJzZXJ2aWNlQHNpeC1pbm5vLmNuIiwiYXVkIjoiaW90X3NhbXBsZV9jbGllbnQiLCJuYmYiOjE3NDk5NTc2OTIsInJvbGUiOltdLCJvcmciOnsibGV2ZWwiOjAsIm9yZ0lkIjoiMGEyYTAwOTMtOGJmNi0xZGRhLTgxOGItZjY0ZTAyMDgwMDAwIn0sIm9wZW5JZCI6IjBhMmEwMGIxLTk2MzQtMTM4MS04MTk2LTM0NWM4NmExMDAwZCIsInNjb3BlIjpbIm9wZW5pZCJdLCJpc3MiOiJodHRwczovLzA4ZDdkYi5hcHAuc2h1aGVuZ2xpYW5jaGFuZy5jb20iLCJleHAiOjE3NDk5NzU2OTIsImlhdCI6MTc0OTk1NzY5MiwianRpIjoiNzEwMDg1NDQtNGRiYS00YTBkLTk3M2ItNjIzMTk1YTExMzE4In0.p10AbEsp5PZyeewQHa2q73rGEt9pr_Z553tzp3ofKQ7aCYGYcR4PU4uleEikKwrNkPWvvPkJf9CDEGHHcv0jrIDVb2LdU6W8AloxP_FEgJZyS1KaxrXAGUs7h1Dj2OhPafW5hc3xy7e8QiMG1NmPXCVTB_x0hc0HmsNc2LDxpjrsyNc1FHnXIDh4IrkowGgJSG-XpPca3n3C11iiS3j6KgEue0No1Ozbh-OYYNvKAa0_DHAWKEvZBEm80LntutMTAmW6eYPNpappmvgZKFq6Zo0xzn0pEJBPJdQQmH36yRaJsCc9WCKuCcPlltvKltz0IjDWpmZbMAfJDJMZyjctAg\",\"scope\":\"openid\",\"id_token\":\"eyJraWQiOiJiYmQ4ZDg0NS0yZTY0LTQxYzQtYTk4NC03Mjg0OWY2OTI1NzIiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJzZXJ2aWNlQHNpeC1pbm5vLmNuIiwiYXVkIjoiaW90X3NhbXBsZV9jbGllbnQiLCJhenAiOiJpb3Rfc2FtcGxlX2NsaWVudCIsImF1dGhfdGltZSI6MTc0OTk1NzY5MSwiaXNzIjoiaHR0cHM6Ly8wOGQ3ZGIuYXBwLnNodWhlbmdsaWFuY2hhbmcuY29tIiwiZXhwIjoxNzQ5OTU5NDkyLCJpYXQiOjE3NDk5NTc2OTIsImp0aSI6ImU2YTQxNWQyLWI5ZmMtNDViZi05MzIwLTlkMjlhYjBmOTFlNiIsInNpZCI6InZkRGY2WWhtOWJTWHdZcVFqdjVwQXBjcHQ3OTFrM1JrcTkxZGFBZEs2V0UifQ.iYcI2BjwQo8msWgNxlghwQS3L8QG0kGvZHVXHeSEjgBRimeYEiT0AWXUxvr_xQNZ3FUD03a1taY_X1vTCiEauaN68pur2cpSRRNxJj1RKPMlMgmKd1xwv5bjiJNdigtsbl9MxCm6U9DqYvQgMMfSV61OJWD_aYagpMAQxAV8qmtInul7wtVyxbYWBpPJYmrsJCM-oYvdAN-6qzL6V8t5VxFTAHiWBQkze6YCoWkmXSi23ssINkg6HIpWFFgsolXtnYnfeQQWMbFo9rTlFaNGtnJqPqdyj5TfaF7tLL5pAZe3l42cXpID2ioKyoU6GTHYC6mGEoclXKbmSfBWojm9tQ\",\"token_type\":\"Bearer\",\"expires_in\":17999}"
},
{
"name": "sourceUserId",
"value": "0a2a00b1-9634-1381-8196-345c86a1000d"
}
],
"scope": [
"openid",
"profile"
],
"property": [
{
"name": "aa",
"value": "bb"
}
],
"exp": 1749957997,
"iat": 1749957697,
"jti": "008eed5f-426f-40e9-b0c6-124da1a05e4b"
}