SSO integration with Salesforce as SP
Salesforce is a cloud-based software that provides customer relationship management (CRM) tools to help businesses connect with customers and prospects.
Assuming you have used Salesforce to manage some parts of your company's business and data, and you intent to extend your solution scope to integrate with other systems and data, you can consider to do the SSO integration of IdP created from SiX IDaaS & IAM tenancy with Salesforce as SP(Service Provider). Since this IdP provide a versatile SSO enablement and integration framework for many applications, you can naturally connect these applications with Salesforce application together.
After you do the integration, Salesforce user can use the user account of IdP from SiX IDaaS & IAM tenancy to sign in Salesforce application, your user data will be connected naturally together. You can leverage this user linkage to connect other system data to streammline your business flows in your whole end to end solution portfolio.
TIP
SSO integration with Salesforce
PS: SiX IDaaS & IAM IDP acts as an federating(intermediary) Identity Provider (IdP) between a primary, upstream IdP (Okta) and a Service Provider (Salesforce).
Steps to integrate IdP with Salesforce as SP
In this integration case, one SiX IDaaS & IAM OAuth client will act as the IdP proxy, when SiX IDaaS & IAM server receive the authentication request from Salesforce, it will trigger an OAuth authentication flow with the IdP(identity application).
TIP
Federated IdP also support the same integration.
1. Create the IdP(Identity application) and an OAuth Client
Refer to Create IdP for SPA
2. Set OAuth Client to integrate with Salesforce
In the OAuth client menu, select "Integrate SSO Application", it will pop up a dialog as below and follow the steps: 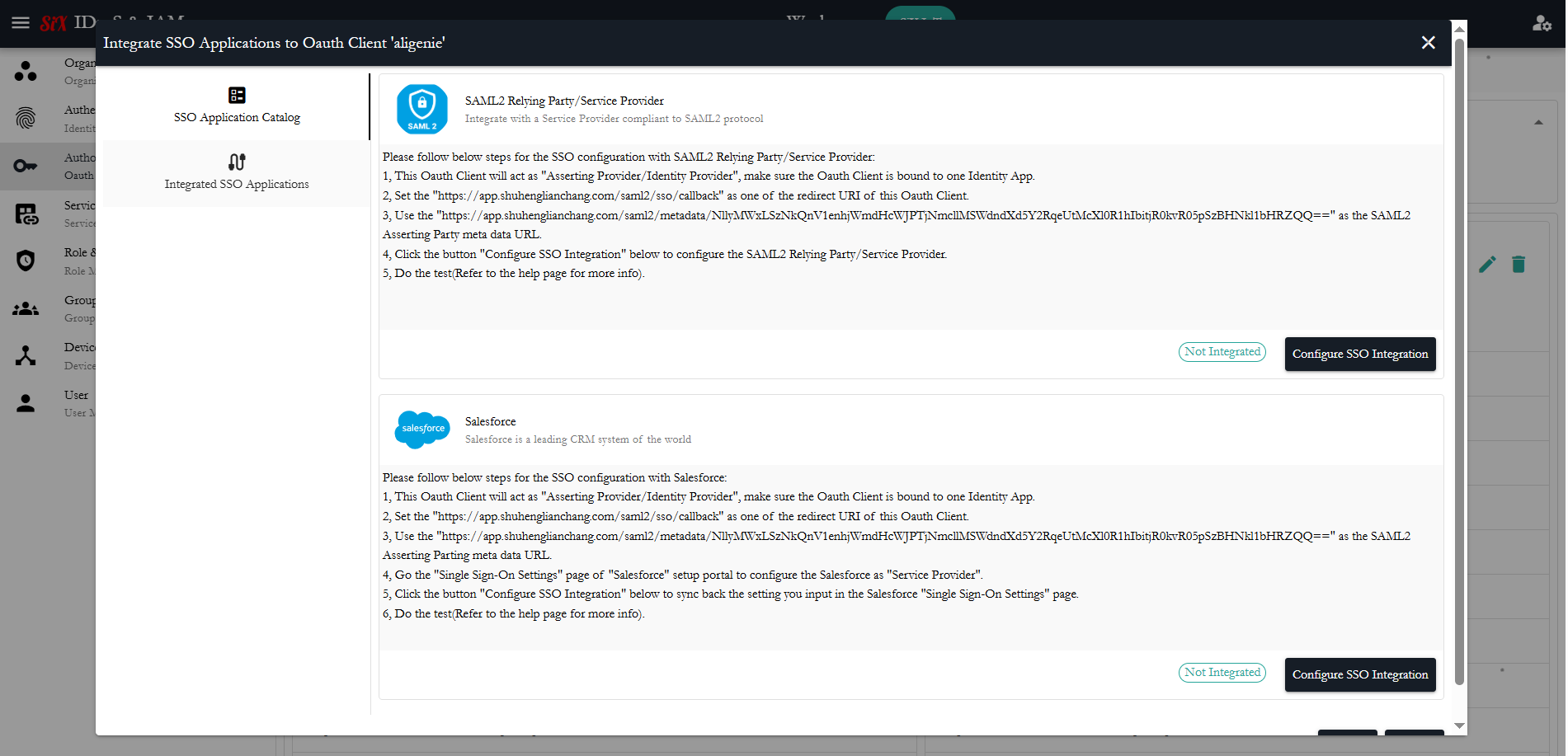
Like you can view the SAML2 meta endpoint and get the meta data as:
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="https://app.shuhenglianchang.com/NllyMWxLSzNkQnV1enhjWmdHcWJPTjNmcllMSWdndXd5Y2RqeUtMcXl0R1hIbitjR0kvR05pSzBHNkl1bHRZQQ==">
<md:IdPSSODescriptor WantAuthnRequestsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>
MIICpTCCAY2gAwIBAgIJAIfcz6WrZjDhMA0GCSqGSIb3DQEBCwUAMBIxEDAOBgNV
BAMTB3NpeC1pYW0wHhcNMjUwNjA1MTQyNDI2WhcNMjYwNjA1MTQyNDI2WjASMRAw
DgYDVQQDEwdzaXgtaWFtMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA
t8fLv5EdfJVe1y7QWcPRv6kMKVqxJt5hJ//TePqR/Cs3mVvtAZmfmFuTR8IhB34k
WGEq8cTlvqn8j/h0fb8Lv0FsXDcKU9ccCCgkXI0aJxOW+RuPy5uSFYNjJvd948tP
x2gFK+Ztps/q3Ismt1P5ovEGcDItUW+edDvm5gL3W1oaKHRrOx7HmVe/ytWHAp30
OxZ86/qVvXd94afu0Gp/Ql6k6x2SQ1XNv7c8on7F31s+3jqSo/F+ffKkiNcL4cqG
7vKNOHtsf9FmuUrvnEH44v+UBhygrTX020xQghXKJXeeZloXSZlG6S2UuLzDozME
8bd9Z1dzwdzBFZDNiPXoYwIDAQABMA0GCSqGSIb3DQEBCwUAA4IBAQCF1uQ4FYLb
wo0tZnEcUsSipye2HVdIDe1zsVJ9LpRj7tlUwnUVCywF1L7Oe2Yy23mDyvhfv8J2
nO5Rjr9hF4TBNKt/y/one4KuQUyATKnk7J2sCMws13v7P14vY7ngh7elk4/4Z3+8
w5JFT4rPUh6TVUWlS4kJX9Ul4XvBH9QyBF2iEvU0rT7fHtZhGmkfg1qzG0q1ujQT
28FzfAvZ9tjZzsgm05+HiiodtSsyltpX6eCIZdZsBqpzTpgnK4kBOYjzmAW+/4XH
Cl0Mf/ElP6OzswqaXJzVKXxt8PY2hhtdVzozCRRiFNWJ5ZGaUH0annfCkbbcNZJV
m7KR24NSyf0l
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://app.shuhenglianchang.com/saml2/slo/NllyMWxLSzNkQnV1enhjWmdHcWJPTjNmcllMSWdndXd5Y2RqeUtMcXl0R1hIbitjR0kvR05pSzBHNkl1bHRZQQ=="/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://app.shuhenglianchang.com/saml2/slo/NllyMWxLSzNkQnV1enhjWmdHcWJPTjNmcllMSWdndXd5Y2RqeUtMcXl0R1hIbitjR0kvR05pSzBHNkl1bHRZQQ=="/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</md:NameIDFormat>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://app.shuhenglianchang.com/saml2/sso/NllyMWxLSzNkQnV1enhjWmdHcWJPTjNmcllMSWdndXd5Y2RqeUtMcXl0R1hIbitjR0kvR05pSzBHNkl1bHRZQQ=="/>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://app.shuhenglianchang.com/saml2/sso/NllyMWxLSzNkQnV1enhjWmdHcWJPTjNmcllMSWdndXd5Y2RqeUtMcXl0R1hIbitjR0kvR05pSzBHNkl1bHRZQQ=="/>
</md:IdPSSODescriptor>
</md:EntityDescriptor>3. Configure the Salesforce SAML client parameters
Click "Configure SSO integration" button in the "Salesforce" pane, you get below dialog and input the parameters you get from Salesforce: 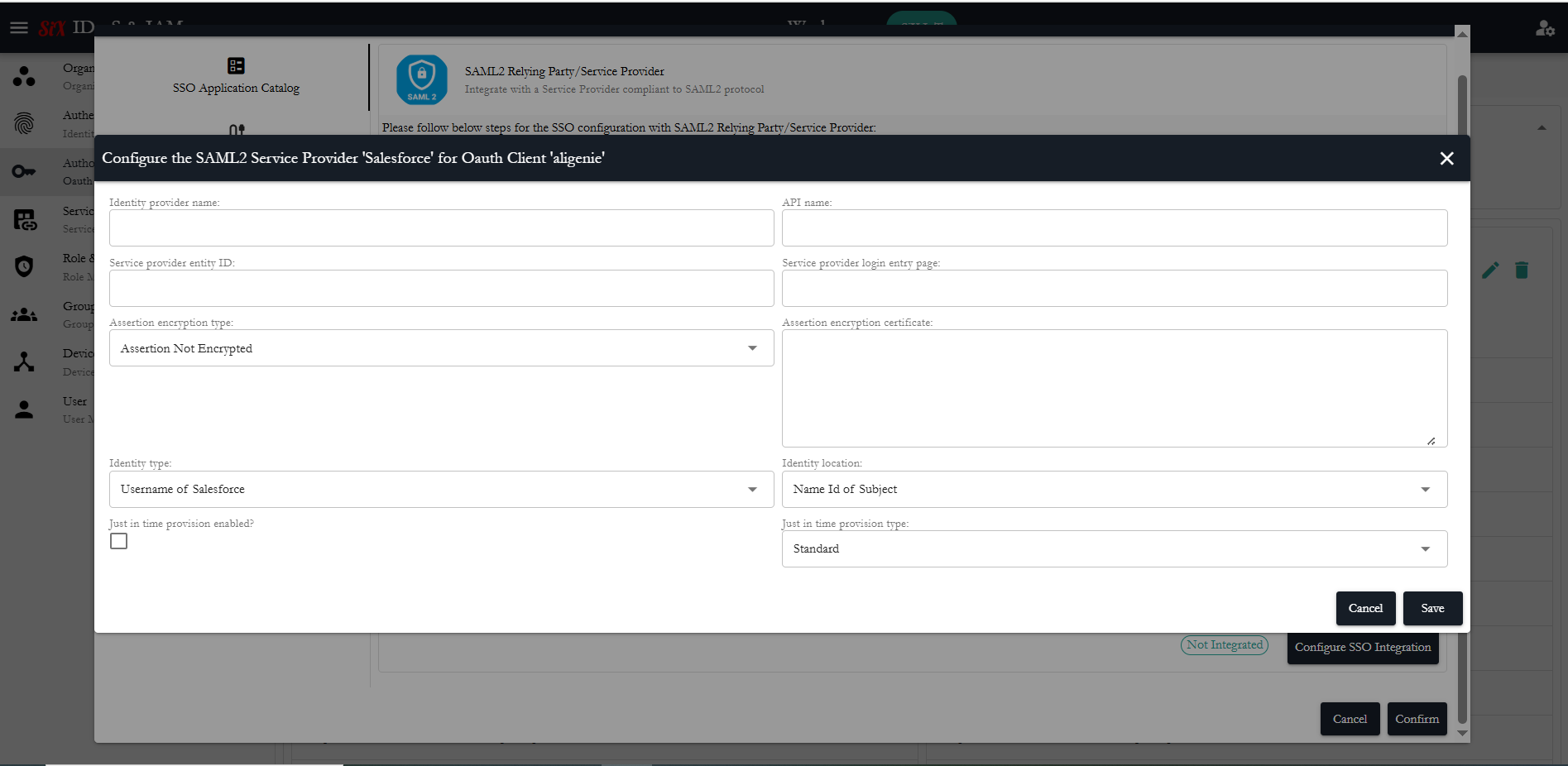
4. Trigger the SSO flow from Salesforce signin page
When you trigger an SSO signin from Salesforce signin page, you will be navigated to the IdP your OAuth client associated.